
New Relic has introduced enhanced features to its Interactive Application Security Testing (IAST) tool, including a novel proof-of-exploit reporting function for more effective application security testing.
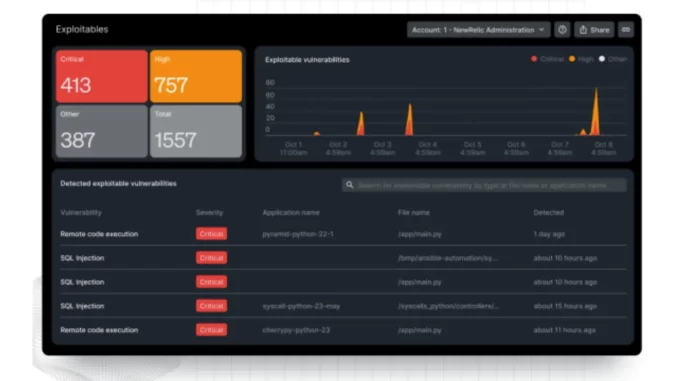
This update allows New Relic’s users to pinpoint exploitable vulnerabilities within their applications uniquely, providing them the capability to replicate the issues for easier remediation of the specific security threats before the release of new software versions. This advancement aids both security and engineering teams in concentrating their efforts on genuine application security issues, ensuring no false positives, according to New Relic.
The introduction of proof-of-exploit reporting significantly enhances the application security testing process, enabling New Relic customers to identify, verify, and fix exploitable vulnerabilities more efficiently.
This approach ensures that teams can confidently deploy new code, backed by the assurance of a 100% accuracy rate in detecting real security problems, as validated by the industry-recognized OWASP benchmark.
“Security must be ingrained in the development culture, not just added on. New Relic IAST offers engineering and IT teams the ability to identify real application security risks with the same platform they use to monitor application performance,” said Manav Khurana, chief product officer at New Relic. “It strengthens DevSecOps by bringing developers and security teams together to write secure code that defends against the threats of tomorrow and promotes a proactive stance on security. For well over a decade, the New Relic full-stack observability platform has bridged organizational silos by providing a single, trusted source of truth and unified user workflows – and now New Relic IAST furthers this mission.”
Other new updates include a new risk exposure and assessment feature that provides visibility into every code change and instant impact analysis, which details the number of applications that would be impacted by a vulnerability.
